Hybrid Work Policy for 2025: Principles, Templates & Governance

TL;DR
- A hybrid work policy formalizes how teams operate between remote and in-office work.
- It defines eligibility, norms, security, and performance expectations to maintain fairness and accountability.
- Without a defined policy, hybrid models risk communication gaps, bias, and compliance lapses.
- Modern policies must be outcome-based, inclusive, and measurable across tools like Slack and Jira.
- How companies can automate visibility, approvals, and documentation across distributed teams.
What You’ll Learn
- How to structure a hybrid work policy for engineering, IT, and cross-functional teams.
- The five principles that ensure fairness, clarity, and measurable outcomes.
- Copy-ready sections for eligibility, working norms, and security compliance.
- How to operationalize enforcement directly inside Slack + Jira.
- Risk and control measures for secure hybrid operations.
- How to communicate your policy effectively through TL;DRs, FAQs, and manager enablement.
Introduction
Hybrid work is no longer a temporary experiment, it’s the operational default for high-performing digital organizations. Yet, most companies still run hybrid setups without a defined policy framework. That gap often leads to inconsistent expectations, compliance risks, and performance blind spots between teams that work differently.
A hybrid work policy provides structure in this fluid environment. It sets the rules of engagement, how and when people collaborate, how work gets measured, and how data stays secure, without prescribing where work happens. For IT, engineering, and service organizations, it’s especially critical: distributed systems, sensitive data, and continuous delivery require alignment and accountability across locations and time zones.
With 2025 close to being wrapped up, leaders are moving from “flexibility-first” slogans to outcome-first operations. That shift demands measurable transparency, inclusive practices, and automation built into daily workflows. A well-crafted hybrid work policy achieves this through three fundamentals:
- Clarity: defines who can work hybrid and under what conditions.
- Consistency: ensures equity and standardization across departments.
- Control: enforces compliance, visibility, and reporting through integrated systems.
Policy Principles
A sustainable hybrid policy isn’t about monitoring presence, it’s about ensuring predictable outcomes and accountable collaboration regardless of location. Modern policies are guided by three pillars: outcomes > attendance, inclusivity, and auditability.
1. Outcomes over Attendance
The old metric of “seat time” no longer applies. Hybrid work policies should define performance based on deliverables, SLA adherence, and velocity metrics, not on time spent online or in-office.
- Anchor team performance to objective indicators such as resolved tickets, sprint velocity, or on-time delivery.
- Replace attendance logs with Jira-linked reporting or Troopr Check-ins, where daily updates roll into shared dashboards automatically.
- Emphasize asynchronous progress visibility to respect focus time while maintaining accountability.
2. Inclusivity by Design
Proximity bias, favoring in-office employees remains one of the biggest hybrid risks. Inclusive policies ensure that opportunities, recognition, and promotions are tied to impact, not visibility.
- Define clear documentation standards for all decisions, ensuring remote participants have equal access.
- Mandate hybrid-friendly meeting formats (recorded sessions, documented decisions, shared notes).
- Encourage managers to conduct equity reviews quarterly, tracking visibility and project exposure across distributed teams.
- Promote cultural rituals (async check-ins, cross-time-zone retros) that normalize distributed participation.
3. Auditability and Transparency
Governance is only real when it’s verifiable. Auditability means every action, approvals, exceptions, and escalations, is traceable without additional overhead.
- Use platforms that log all approvals and updates within your collaboration tools (e.g., Slack threads synced to Jira).
- Integrate SSO, SOC 2 Type II protocols, and activity logs into policy compliance sections.
- Define retention periods for communication records, ensuring consistent audit trails across distributed teams.
Troopr in Practice: Troopr enables this by automatically syncing Slack actions (approvals, updates, SLA triggers) to Jira tickets. Managers gain a verifiable, timestamped trail of every decision, vital for audit readiness and ISO/NIST-aligned governance.
Eligibility & Exceptions (Role-Based)
Define who qualifies for hybrid work and under what conditions exceptions apply.
Template:
- Eligible employees include full-time team members whose roles can be performed remotely without compromising security or service delivery.
- Ineligible roles include those requiring physical access to secure environments, specialized hardware, or on-site client interactions.
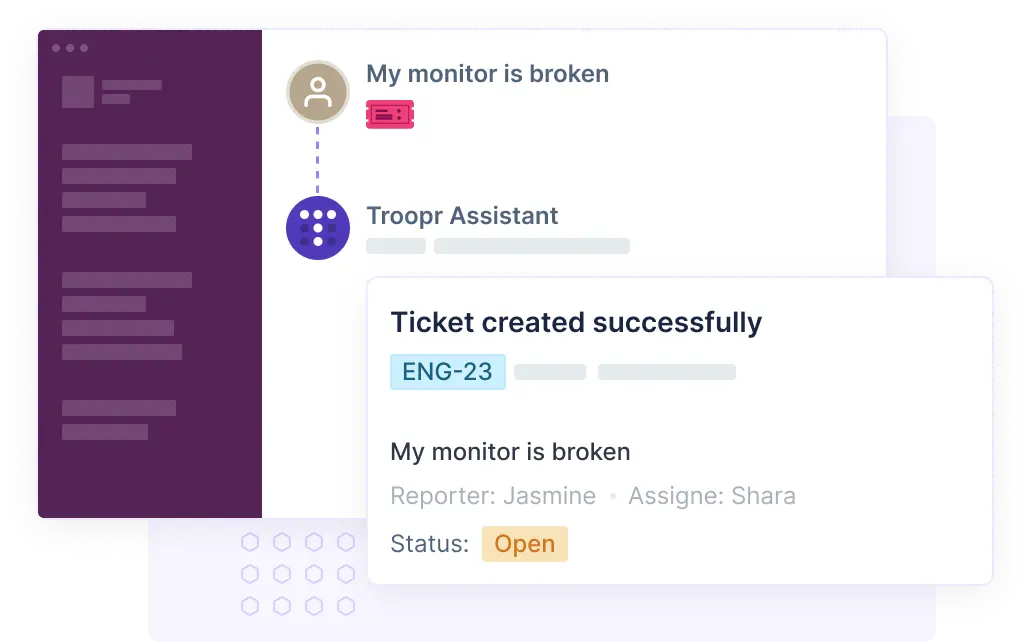
- Exceptions must be approved by department heads and recorded in Slack via a Troopr workflow linked to Jira for traceability.
- Temporary exceptions (e.g., travel, medical, infrastructure) require a documented duration and auto-expire after review.
Troopr Tip: Automate exception requests in Slack. A manager’s approval can trigger a Jira comment or issue update, creating an instant audit trail.
Working Norms (Response Windows, Meeting Rules, Decision Logs)
Hybrid productivity depends on clear communication standards that remove guesswork and maintain visibility.
Template:
- Response window: Acknowledge messages within 4 working hours during core overlap time (e.g., 10 AM–4 PM local).
- Meeting hygiene:
- Default to async standups using Troopr Check-ins.
- Record and document all live sessions; post summaries to shared Slack channels.
- Mandate agendas and end with clear owners + Jira task references.
- Decision logs: All key technical or project decisions must be recorded in the appropriate Jira issue or Confluence page, auto-notified in Slack.
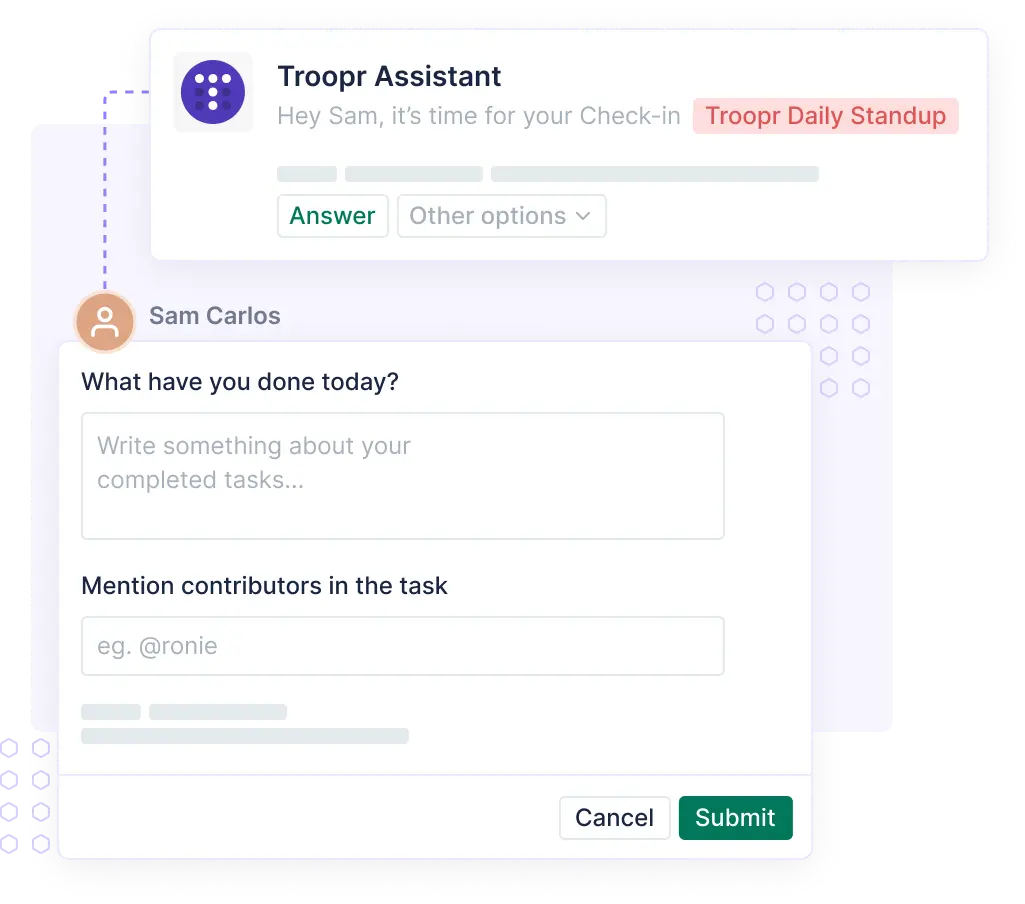
Troopr in Action: Engineering teams use Troopr Check-ins to replace daily meetings, link updates directly to Jira tickets, and send automated summaries to team channels, reducing sync time while improving traceability.
Security & Compliance (SSO, Encryption, Incident Handling)
Security remains the non-negotiable core of any hybrid policy, especially for Engineering and IT functions.
Template:
- All systems must be accessed via SSO with enforced MFA.
- Company data must reside only in approved, encrypted storage.
- Incident reporting:
- Employees must report suspected data or access breaches within 2 hours using the #incident-report Slack channel.
- A Troopr automation can create a Jira Service Management ticket tagged “Security Incident.”
- Quarterly compliance audits ensure adherence to SOC 2 Type II, encryption standards, and RBAC configurations.
Troopr Compliance Layer: Every alert, approval, and escalation logged via Troopr becomes part of your immutable activity history, supporting ISO and SOC audit requirements.
Learn More on: Hybrid Work Schedule Templates & Rollout
Equipment & Reimbursements
Clarity on equipment policies reduces ambiguity and ensures equitable access to productivity tools.
Template:
- Company will provide or reimburse approved equipment for hybrid employees (laptops, monitors, headsets, internet boosters).
- Employees are responsible for maintaining physical security of devices.
- Reimbursements must be submitted through the approved HR system; eligibility capped as per role.
- Record all issued assets under IT’s inventory system, cross-referenced with Jira asset modules.
Metrics & Reviews (Quarterly)
Measurement ensures hybrid success remains visible and actionable.
Template:
- Teams will review hybrid work outcomes quarterly, focusing on:
- SLA adherence (incident response, resolution times).
- Velocity metrics from Jira.
- Employee engagement (check-in consistency, participation).
- Use Troopr Reports in Slack to share results automatically.
- Policy compliance metrics (security incidents, audit trails, missed SLAs) will be reviewed at the leadership level every quarter.
Enforcement via Slack + Jira
A hybrid work policy fails without consistent enforcement and enforcement fails without systems integration.
For Engineering and IT teams, Slack and Jira already represent the daily workflow. Embedding policy governance directly into these tools removes friction, prevents exceptions from going unnoticed, and turns every update into an auditable record.
The goal isn’t policing, it’s visibility without overhead.
Further Reading: Distributed Team Management Metrics: Slack + Jira Visibility Framework
Channel Conventions; Auto-Posted SLAs; Incident Templates
A lightweight enforcement model starts with standardized channels and automated service-level communications.
Channel Conventions:
- Use dedicated channels per function (e.g., #dev-ops, #incident-triage, #service-requests).
- Prefix conventions like #proj- or #ops- for easy filtering and governance tracking.
- Restrict confidential channels with RBAC-based access via Slack Enterprise Grid.
Auto-Posted SLAs:
- Integrate Jira SLAs into Slack using Troopr Reports.
- Example: every Monday, a Troopr bot posts unresolved ticket summaries and SLA countdowns in the relevant service channel.
- Managers can acknowledge or reassign tickets directly from Slack, with every action updating Jira automatically.
Automating Approvals and Exception Trails
Hybrid policies thrive on clarity and accountability, both of which depend on auditable approval processes.
Manual approvals, email threads, or DMs make enforcement impossible to scale.
Automation Framework:
- Trigger: Employee submits an exception or policy-related request (e.g., travel, asset, remote setup) via a Troopr form in Slack.
- Approval Workflow: Manager receives a Troopr prompt in Slack → approves/denies inline.
- Record Sync: Troopr automatically updates the corresponding Jira issue with decision notes and timestamps.
- Audit Trail: Each transaction becomes searchable by user, date, and policy tag.
Read More: Remote vs Hybrid in 2025
Use Cases:
- Work-from-another-city requests.
- Extended offline or deep-work schedules.
- Hardware or reimbursement approvals.
- Incident escalation authorizations.
This model eliminates the need for external tracking sheets or manual logs while meeting compliance expectations for traceability and access control.
Risk Register & Controls
Hybrid work introduces new vulnerabilities, often not from malicious intent but from distributed habits: personal devices, unauthorized apps, and informal data sharing.
A well-built policy must recognize these risks and map them to preventive controls embedded in the organization’s digital stack.
Data Leakage, Shadow IT, and Social Engineering
Even mature teams experience accidental or opportunistic data risks. The following categories form the baseline of a hybrid risk register.
1. Data Leakage
- Risks: Sensitive data shared over personal Slack messages, unencrypted file uploads, or screenshots in public channels.
- Controls:
- Enforce workspace-wide DLP policies and content scanning.
- Configure Slack Enterprise retention for regulated data.
- Mandate encryption in transit and at rest for all integrated tools.
2. Shadow IT
- Risks: Use of unauthorized SaaS tools or personal automation bots that bypass IT review.
- Controls:
- Maintain a live app allowlist with versioning in Confluence or Jira.
- Auto-alert IT when unapproved integrations are detected via Slack’s audit logs or SIEM connectors.
- Integrate app onboarding requests with Troopr approval workflows to preserve audit history.
3. Social Engineering
- Risks: Phishing, impersonation via Slack DMs, or unverified channel invites.
- Controls:
- Enforce SSO and MFA everywhere.
- Restrict external invites and use workspace-approved naming conventions.
- Conduct quarterly awareness refreshers, tracked via Jira training tickets.
Troopr Advantage: Each of these controls can be tracked automatically through Troopr workflows. For instance, if a user installs a new app, a Troopr alert can open a Jira compliance issue tagged “Shadow-IT Review,” ensuring visibility before exposure escalates.
Mitigations: App Allowlist, Bot Scopes, Retention Policies
Once risks are identified, define mitigation controls in your policy, clear, enforceable, and tool-linked.
1. App Allowlist
- Maintain a single authoritative list of approved apps and APIs.
- Link it to a public Confluence or Jira page tagged #compliance.
- Require IT approval for any new integrations through Troopr’s Slack-based request form.
- Review the list quarterly during hybrid policy audits.
2. Bot Scopes and Permissions
- Grant the minimum required scopes to Slack bots and integrations.
- Disable direct message access for automation bots unless needed for check-ins or incident notifications.
- Record every granted scope in the Jira configuration log for traceability.
- When decommissioning tools, revoke OAuth tokens and document removal actions.
3. Retention and Archival Policies
- Define data retention timelines by channel type:
- Project channels – 18 months
- HR/compliance channels – 7 years
- Incident channels – permanent or per legal requirement
- Use Slack’s retention policies and Troopr’s auto-archival reminders to maintain hygiene.
- Back up essential records to compliant storage (AWS S3 with encryption or your internal archive system).
Communicating the Policy
A hybrid work policy is only effective if it’s understood, adopted, and referenced. Most policies fail not in design but in delivery.
Contextual Reading: Hybrid Work Playbook 2025: Models, Automation & Outcomes
Your communication plan should treat the policy like an evolving product, with a concise summary, manager enablement tools, and a living documentation process.
One-Page TL;DR
Every employee should grasp the policy’s essentials in under five minutes.
Publish a single-page summary, preferably in Confluence or Slack pinned message covering:
- Eligibility: Who can work hybrid and approval flow.
- Norms: Expected response and collaboration patterns.
- Security: Mandatory access and compliance guidelines.
- Equipment: What the company provides or reimburses.
- Review cadence: When outcomes are measured and by whom.
Tip: Use a Slack workflow to share the TL;DR automatically with new joiners, linked to the full policy doc in Confluence.
Manager Enablement
Managers translate policy into daily behavior. Equip them with ready-to-use templates, reminders, and escalation playbooks.
Checklist:
- Sample team-level hybrid charter (meeting cadence, communication stack).
- “First 30 days” onboarding guide for new hybrid hires.
- Slack message templates for incident, exception, or approval communications.
- Quarterly Troopr Check-in templates for visibility and workload reviews.
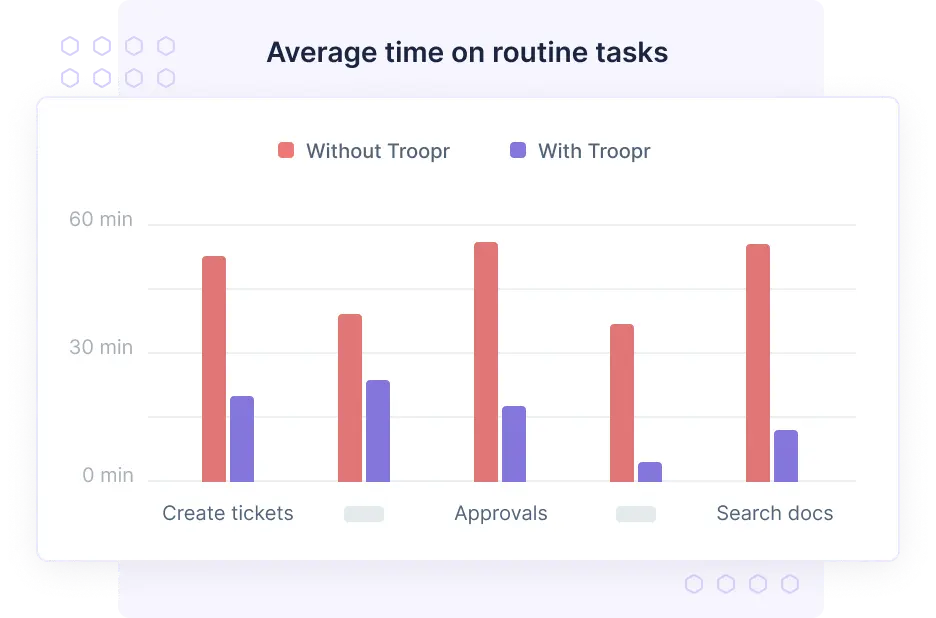
Enable managers to track adherence with Troopr Reports, e.g., monitoring missed check-ins, sprint delays, or SLA breaches—all visible in Slack.
FAQ Living Doc
Turn recurring employee questions into a living FAQ, not a static page.
Link it directly within Slack (#policy-faq channel) so updates are continuous.
Sample entries:
- “Can I work from another city temporarily?”
- “How do I report a data breach?”
- “What’s covered under equipment reimbursement?”
- “How are SLAs tracked for hybrid incidents?”
- “Who audits compliance and when?”
Each answer should reference a Jira issue type or Slack workflow, creating a transparent map between questions and accountable actions.
FAQ: Hybrid Work Policy
1. What is a hybrid work policy?
A formal framework defining how employees split time between remote and on-site work, covering eligibility, communication norms, and compliance expectations.
2. What should a hybrid policy include?
Eligibility rules, working norms, data security, equipment guidelines, and review metrics. For IT and Engineering, it should also cover auditability and tool usage.
3. How can companies enforce a hybrid work policy?
By embedding approvals, reporting, and SLAs into existing systems like Slack and Jira using automation tools such as Troopr.
4. How do hybrid policies handle data security?
They enforce SSO, encryption, app allowlists, and retention policies. Every access, change, and exception should be logged for audit readiness.
5. What’s the review cadence for hybrid policies?
Quarterly reviews, including performance metrics, SLA adherence, and inclusivity audits.
6. How does Troopr support hybrid governance?
By connecting Slack and Jira, automating reports, and logging every decision, Troopr ensures measurable, compliant hybrid operations.
7. Will work-from-home end in 2025?
Unlikely as the data shows hybrid is now the dominant model. The future lies in measurable flexibility, not full reversion to office-only setups.

.svg)



